Recently, I deployed vCloud Director 10.4.1 after all the configuration I noticed that /provider is still accessible from the internet, which is not needed and will unnecessarily invite security risks. I turned to google with this query but nothing relevant came up. So here I am writing about it so this becomes a relevant post.
What is vCloud Director?
vCloud Director is one of the most popular Cloud Service-Delivery Platform, allowing providers to Operate and manage successful cloud-service businesses with ease.
In this post, We will see how to block the provider (https://vcd-ip.local/provider) and /cloudapi/1.0.0/sessions/provider URIs access to the vCloud Director using NSX-T. We can configure various security settings through NSX-T. For example, we can enable HTTP redirect, limit the number of connections, or restrict access based on the user’s IP address.
I am using vCloud Director 10.4.1 and NSX-T 3.2.1.2. (It is assumed that you have already deployed and configured the load balancers for vCloud Director) Here’s a Nice blog on VCD configuring NSX-T LB for VCD and on how to renew the cell certs if they are expired.
Step 1
Login to NSX-T
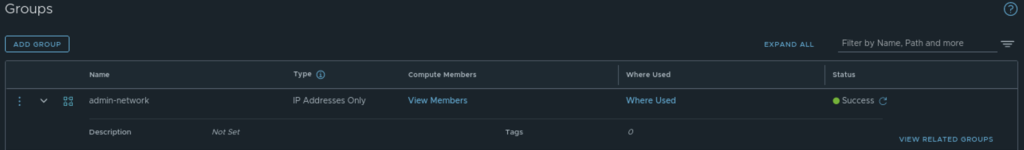
Create a group called admin-network and give the IP address to which you want to allow access to /provider
Inventory -> Groups -> Add Group
Note: I have added the IP address to which I want to allow access.
Step 2
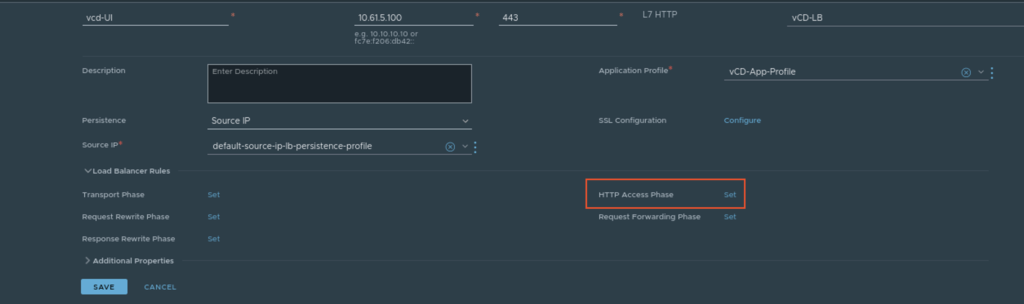
Let’s create the Rules under Load Balancer
Networking -> Load Balancing -> Virtual Server -> Edit the Virtual Server you have configured for VCD, Expand the Load Balancer Rules, and click on set Rules
Step 3
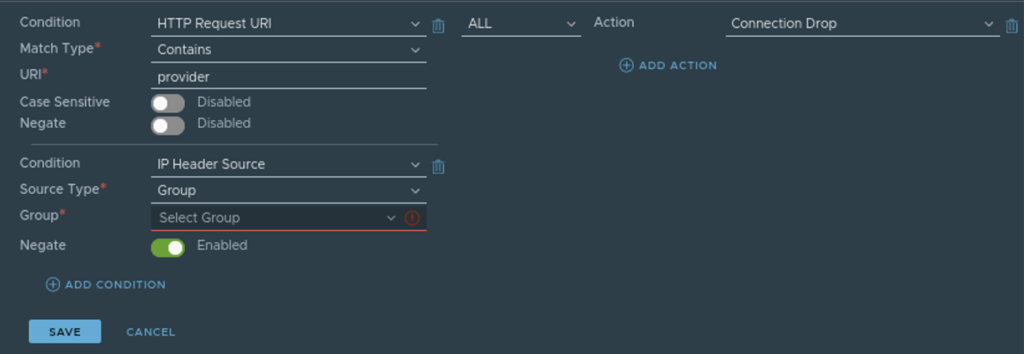
Add HTTP Access Rules as follows, we will create 3 rules.
- Block all URi that contains provider (URLs with /provider in it)
- Block All arguments with provider (anything after ? in URL)
- Block API for provider (/sessions/provider or /cloudapi/1.0.0/sessions/provider)
We will drop all the incoming connections to URI and URI Arguments that contain “provider” except if it is requested by the users who are part of the group we created in Step 1.
Make sure to Negate is enabled as 2nd condition which is to allow access. 1st condition blocks the access and 2nd condition allows it. I have created 3 different rules.
All 3 rules!
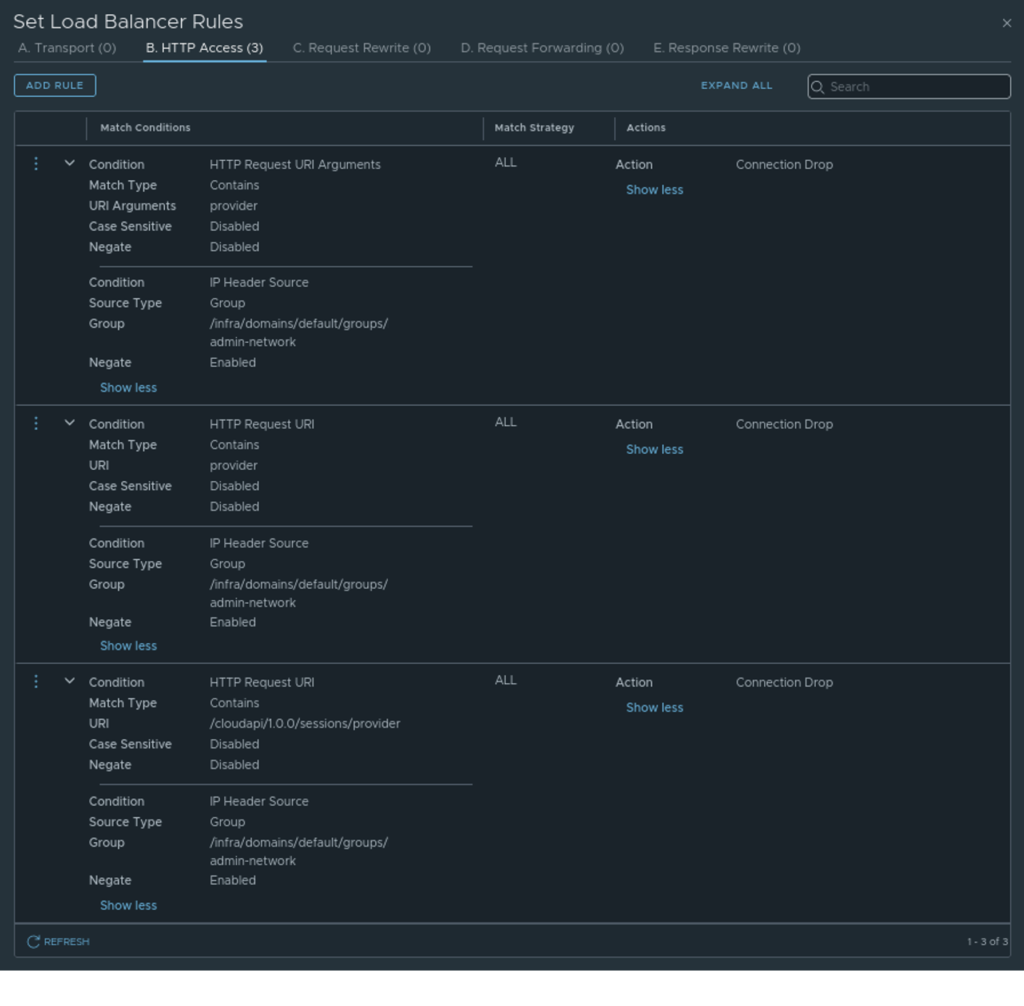
Now only the users from the admin-network group will be able to access /provider URIs, anyone else trying to access /provider URI, LoadBalancer rule which we created will drop that connection. Which should look something like this.
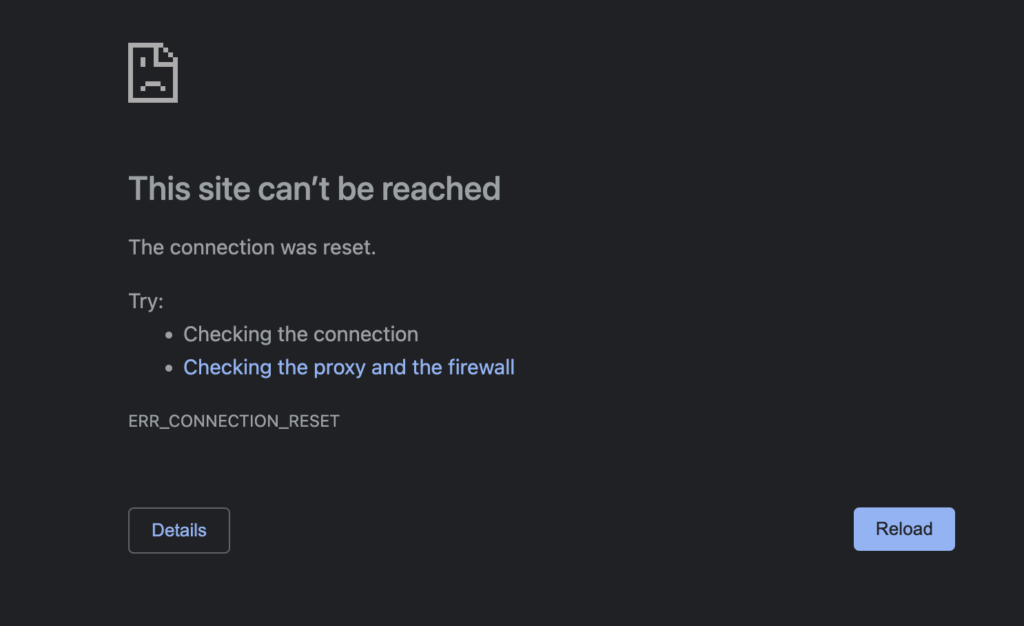
Hope this helps.
