ESXi host SSH RSA key fingerprints and SSL thumbprints are important security measures that help to ensure the authenticity and integrity of your ESXi hosts. These fingerprints are unique identifiers that are generated for each host and can be used to verify the identity of the host and establish a secure connection. In this post, we’ll see how to generate ESXi host SSH RSA key fingerprints and SSL thumbprints.
Below commands will be required in the deployment workbook when you deploy cloud builder for VCF bringup. You can use an automated script to deploy VMware Cloud Foundation with Nested ESXi hosts.
First, let’s take a look at how to generate ESXi host SSL Thumbprint . There are multiple ways for it, let’s see three of them.
Option 1 (ssh into the ESXi Host)
SSH to the ESXi host using and run the following command (I am using sha256 as I want these to fill in my VCF deployment parameter workbook.)
openssl x509 -in /etc/vmware/ssl/rui.crt -fingerprint -sha256 -nooutOption 2 (From outside ESXi host)
echo -n | openssl s_client -connect hostip:443 2>/dev/null | openssl x509 -noout -fingerprint -sha256Option 3 (From DCUI)
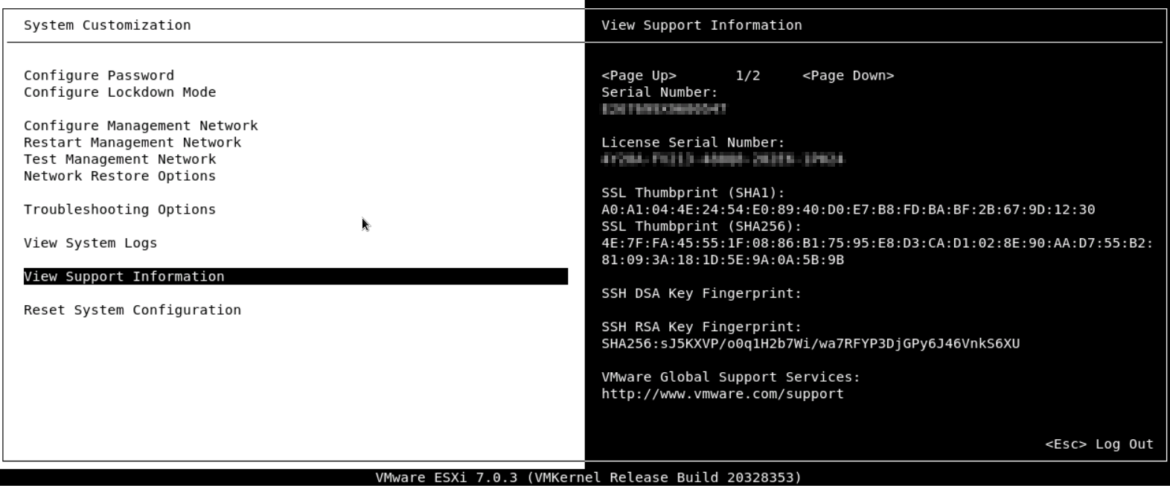
Open your ESXi DCUI and check View Support Information
SSH RSA Key Fingerprints
To retrieve SSH RSA Key Fingerprints (SHA256) use the following command. (Note: SSH has to be enabled on the host to get the output)
ssh-keygen -lf <(ssh-keyscan hostname 2>/dev/null)
Hope this helps!